October 21, 2024
Jabber.org Notices



Releases have happened recently that revolve around Poezio, a TUI (Terminal UI) client for XMPP, including Poezio itself, its backend XMPP library Slixmpp, and also the poezio and slixmpp plugins for OMEMO.
Mathieui has already made a proper release note for Slixmpp and I invite you to read it! It includes many bugfixes of course, and internal changes around async handling, that may reflect on some of the APIs you are using.
Poezio has also seen many improvements.
Internally, for one, our default branch has also been moved to “main”, many type hints have been added, implicit casts (safeJID) have been removed, lots of event handlers and calls are now async, APIs from Slixmpp are being used instead of redoing our own, many refactoring, various performance improvements.
Pypy3 support was removed because it was causing many users to use the cffi
module specifically implemented for pypy3 instead of the more performant C
implementation. For those who are running from sources and not using the
update script, don’t forget to run make to build the C module.
A license change has happened, and Poezio is now under GPLv3+! While I am not exactly in favour of intellectual property1, this is a straightforward lever we have against capitalism2. Poezio being a prime resource for Slixmpp examples, GPL code should reasonably ensure that the 4 freedoms reach end-users. In practice, this should allow for poezio-omemo to be merged into Poezio. I am now personally hoping for Slixmpp to change its license as well.
And other changes more visible to users! To name a few, quality of life
improvements such as xmpp:...?join URIs handling in /join, impromptu rooms
creation is now more reliable and creates rooms with shorter names, and tab
names in the activity bar can be colored using Consistent Color
Generation by setting autocolor_tab_names
to True. Read more in the changelog.
 The tab name color on top can also be reversed
(foreground/background) in the theme to look the same as the activity bar
below.
The tab name color on top can also be reversed
(foreground/background) in the theme to look the same as the activity bar
below.
Plugins have seen changes as well. A new untrackme plugin replaces the now
deprecated remove_get_trackers. Link Mauve has also developed
a sticker plugin (to send them), similar in essence to what Movim
has been doing for ages. Rich presence (activity, gaming, mood and user tune)
has been removed from Poezio core and moved in the user_extras plugin. And
again many fixes.
Many of these fixes have been realized by mathieui, who is by far the biggest committer on the release, and in general probably the person with the best understanding of the project. Thanks also to louiz for providing the infrastructure all this time, and to eijebong, Ge0rG, Kaghav Gururajan, kaliko, Thomas Hrnciar, jonas’, and southerntofu for the many patches.
Archive handling (MAM) was already in the previous release, but has been reworked and should now be more reliable.
When opening a tab, Poezio will fetch 2 screen pages worth of messages if it has no logs for this tab. Archives are automatically stored locally if configured (default), in which case they won’t be re-downloaded but read from the local copy directly the next time they’re requested.
To read older chat messages in a tab, just scroll up with PageUp and Poezio
will fetch more automatically if it needs to.
This is configurable with options that have been introduced such as
mam_sync or mam_sync_limit to enable/disable
the use of MAM and how many messages to fetch at most. And
use_log also configures the fact that archives are stored
locally.
Some work around storing message IDs – that our log format doesn’t do – will be needed in the future to allow for easier message deduplication.
The Poezio E2EEPlugin API has been improved to accommodate changes in
poezio-omemo, slixmpp-omemo and changes of the OMEMO backend library. Two
plugins which are also seeing changes!
Heartbeats are now supported. Heartbeats are meta-messages which transfer only cryptographic key material (nothing else) and are used to strengthen OMEMO’s forward secrecy. This is particularly relevant on clients like Poezio that can stay running in the back for some time, receiving messages without replying.
Some other changes include colored fingerprints using the Consistent Color Generation document – such as specified in the current (0.8) OMEMO spec – and sending encrypted media (aesgcm URIs).
What hasn’t changed is that this plugin lacks a UI and trust management. Hopefully this should come soon, with a little motivation to do UI work.
All in all, there aren’t (m)any revolutionary changes, but with these releases come many fixes for paper cuts that hopefully make users happier. This makes me think that even though Poezio is far from being perfect, there doesn’t seem to be many important things missing.
There are however changes that would require a lot of refactoring, such as a multi-account feature, or easier maintenance in general.
We have decided to start migrating Poezio to Rust, in part to be able to refactor the project more easily, and also because it’s a language we’ve come to appreciate over the years with experience in other projects, and more specifically with xmpp-rs, an XMPP library in Rust.
All of this will happen right after the release, and we invite interested people to join the effort!
P.S.: I am looking for poezio screenshots with various setups to display in
public places, under a free license. Please send me your screenshots in
relatively high quality at blog at bouah.net. And don’t forget to ask
pixels appearing on the image for permission!





We are proud to present to you yaxim version 0.9.9 “FOSDEM 2020 Edition”. Many things have changed under the hood (reliable messaging with MAM and Push, new UI with runtime permissions), and some exciting new features like even easier onboarding, service browsing and Matrix support. Taken together, yaxim now fulfills the Core IM and the Advanced Mobile profiles of the XMPP Compliance Suite 2020.

Starting with this version, yaxim follows Google’s “Material Design” style. To comply with last year’s strictened Google Play publishing requirements, we had to replace the deprecated ActionBarSherlock library with Google’s own appcompat, which provides the Material style.
This also means that yaxim now requires at least an Android 4.0 device. As 4.0 was released in 2011, this only affects a single-digit number of devices. Users with a ten years old phone need to stay with older yaxim versions, which run on Android 2.3+.
Furthermore, on Android 6+ devices, the user will be asked to grant permission at the moment when they are actually needed (i.e. when sharing a file or taking a photo).

On Android 8+, the new notification channels are used by yaxim. A new channel will be created for each contact with a custom ringtone. Once you receive a message from such a contact, you need to use the Android notification settings to change the ringtone, though.
yaxim 0.9 introduced Easy XMPP, using the purely client-side XEP-0379: Pre-Authenticated Roster Subscription, which required a server with active In-Band Registration.
The new XEP-0401: Easy User Onboarding allows you to invite new users to your server without being abused by spammers.
Here, you can see a poezio user on a prosody server creating an invitation that is used by yaxim to register and auto-add the inviter:
The invitation page in the example is making use of Google Play Install Referrers to let the newly installed yaxim know the inviter’s address, which has a privacy impact, and therefore is not rolled out to the official landing page yet.
There is a new view of your (bookmarked) rooms and a browser of public rooms powered by search.jabber.network.

Your nickname (“display name”) is now synchronized to the server using XEP-0172: User Nickname, and you can change it in the account settings.
The room browser can also be used to discover services by entering a valid XMPP address into the search field:



This is not limited to servers and rooms, you can also search for users, chat with them and add them to your contact list:

While initially introduced as an
April Fools’ Day joke,
Matrix support (using the
Bifröst bridge is now
actually integrated into yaxim, using the official bridge on matrix.org,
which has also been made ready for FOSDEM 2020.
For users who are using yaxim in parallel to another client, the new support for XEP-0313: Message Archive Management (MAM) is good news. When connecting to the server, yaxim will now activate MAM and request all messages since the last synchronization. This will ensure that yaxim receives all messages which already were delivered to the other client.
Furthermore, when installed on devices with Google Play Services, yaxim will
register for XEP-0357: Push Notifications via the push.yax.im server.
This will ensure that the app is woken up from deep sleep or launched when
somebody sends you a new message.
These important changes are also reflected in the app privacy policy.
The internal chat message database has been optimized by adding database indexes for all frequent operations, making yaxim much faster at loading chat windows with long histories.
Furthermore, yaxim was upgraded from the ancient Smack 3 to the Smack 4.3.x XMPP library.
This release brings significant changes, and we had hoped to be able to finalize even more to make a glamorous and exciting 1.0 release for the 10 years anniversary. However, the current code base brings some major improvements for reliability and usability and we did not want to hold them back even further.
More work is needed on the contacts view, to allow sorting by conversation age and to quickly search your contacts. Furthermore, the creation of rooms and inviting your friends into them need to be integrated.
MAM was long overdue, and for now only your private messages are queried for. Room history is still obtained using the legacy mechanism, meaning that sometimes, you might miss out on parts of room history.
The embedded image view does not have proper caching, and it will attempt to load any attachment, regardless its size and whether it can be displayed in yaxim. This needs to be restructured in a way that limits downloads to actual image files of a certain maximum size.
Another episode of the XMPP sprints series happened this weekend close to Stockholm in the Nacka prefecture, in a house we rented. Significant improvements to the sprint infra this time are sauna and crêpes!
We worked together on improving a new groupchat bookmarks specification, file transfer interoperability issues, and a future landing page for new XMPP users! As usual, every developer meetup comes up with its share of bug fixes, new ideas, and improvements.

Last year, Dave Cridland and JC Brand submitted a new specification titled “Bookmarks 2 (This time it’s Serious)”. This XEP didn’t get much attention in the community until this weekend.
As mentioned in a previous article, there are multiple specifications for bookmarks in XMPP, one using the Private XML storage, and another one using PEP as storage. Not so long after the Cambridge sprint last year, Daniel submitted a conversion XEP to facilitate client behaviour and thus user experience.
This new specification also uses PEP as storage but it brings a few improvements to the table. It splits updates to the bookmark storage into per entry operations instead of updating the whole storage at once. This allows for finer grained handling in clients and prevents some race conditions.
The XEP came up with its share of challenges that some of us attempted to fix in a pull request that has been submitted and is now awaiting feedback from the authors.
Bookmarks 2 is now implemented in at least 5 clients, (Conversations, Dino, Gajim, Movim, Renga, and some initial work in poezio), but will not be used as long as the feature is not advertised by the server. A new prosody module is also available for adventurous services operators.
Roel and I worked on an idea that came up at the UX sprint in Brussels in January to have a landing page for new users. This page would recommend a specific server depending on different factors that would be gathered automatically for the most part (if not all). This is more or less similar to other portals like joinmastodon, or nextcloud sign-up process.
Building up the website isn’t the hardest part. What is hard is finding ways to convey to the user what “federation” or “public network” mean. Roel teaches in Interaction Design and was a great help over the weekend. We came up with a narrative for the project and a sketch for a sign-in flow.
The project is far from being over, this is only the tip of the iceberg. Lots of work needs to be done with the “stakeholders”, that is mainly users and server operators.
To know what server to recommend to users we first need to get a list of servers we are confident about and willing to recommend. This would mandate discussing the issue with server operators to get feedback on a required “feature set” and policies. All this would then be fed into usability testing sessions for users to validate all of it. After that, we would need lots of promotion around it and that’s also going to take a significant amount of effort.
While I am excited about all this I don’t think diving in head first is a good strategy and I would rather take it slow.
Pulkomando has been working on implementing IBR support in Renga, and reported with Link Mauve issues about server implementations that weren’t respecting the specification. The issue in prosody has been fixed and one has been opened for ejabberd.
Larma tackled issues with bot bridging where users of bridged networks are displayed as talking through the bot. This happens for example with matterbridge. This could be improved UI-wise but requires some groundwork and spawned discussions about the groupchat protocol in some specific cases.
Fiaxh spent some time improving the empty placeholder for no opened conversations in Dino. Here is a preview:

Other people worked on Jingle File Transfer interoperability. They narrowed down the cause of a somewhat old issue in gajim, discovered an issue with the epoll backend in prosody, and another in dino.
I would like to take this opportunity to remind you that you can also contribute to sprints! If you are a developer, a translator, working on documentation, or in any other way contributing to an XMPP implementation, we encourage you to find 2-3 other people close to you and organize a sprint!
TODO: come up with a platform to show interest close to you.
The XMPP Standards Foundation (specifically the SCAM team) will be happy to help you get it all sorted, and also provide some budget for your event if necessary. Please do contact us!

Starting today, yaxim is switching its protocol foundation from the deprecated exchange of clumsy and inefficient XML streams to the modern and elegant combination of HTTP and JSON/REST, the Matrix protocol.
The XMPP protocol celebrated its 20th birthday early this year. The Matrix followed two months later and is currently in the middle of its own celebration. Some fifteen years later, a small company decided to use the strong brand value of the Matrix name to reinvent XMPP with a modern facade.
Evil voices claim that MATRIX stands for Monolithic, Awefully Trendy Re-Implementation of XMPP, and there is some truth to this, if we compare the words of the respective founding fathers:
Jabber is a new project I recently started to create a complete open-source platform for Instant Messaging with transparent communication to other IM systems(ICQ, AIM, etc).
I think they missed the bit where Matrix is called Matrix because it bridges (matrixes) the existing networks (Slack, IRC, Telegram, Discord, XMPP, etc) in, rather than needing to convince everyone to join.
However, the Matrix protocol has outgrown Vector Ltd, there is a
version 1.0 0.4 specification,
and even a
Matrix.org Foundation.
This is much superior to XMPP, which is based on some arcane specifications maintained by a bunch of grey beards, plus a separate organisation for protocol extensions. In addition, Matrix supports working over 100 bits per second connections, while XMPP only gives you 75 bps.
The monolithic protocol is another huge advantage compared to many hundreds of optional extensions, and the rumors of Matrix fragmentation are a blatant lie.
Therefore, the yaxim developers have decided to take the blue pill, to move forward, and to use the better and more modern and mobile friendly polling based HTTP scheme. Starting with the current beta release, you can enter Matrix chat rooms and talk to users on the Matrix.
The legacy XMPP protocol is remaining in the release for now, but will be removed in the near future to reduce the bloat of yaxim. You will be able to migrate your contacts to your new Matrix account by using the Bifröst bridge.
In parallel, we are working on switching yax.im from prosody to Synapse. The data transition is already completed, and we are only waiting for the data center provider to add 512GB of RAM to the machine before we can switch over.

We're pleased to announce the last release of ejabberd for 2014! Thanks to contributors, this release includes great improvements and opens road to 2015.
ejabberd Community 14.12 includes many bugfixes, and a few new features:

Full announcement: ejabberd Community 14.05: the culmination of a year of change
ejabberd Community 14.05 has great new features, several improvements and many bugfixes over the previous 13.12 release:
ejabberd now includes support for:
- XEP-0198: Stream Management (EJAB-532)






We are pleased to announce a new stable release of ejabberd, ejabberd Community 13.12.
It has several bugfixes over the previous 13.10 release, and a few new features:
As usual, the release is tagged in the Git source code repository on github

We are pleased to announce a new stable release of ejabberd, ejabberd Community 13.10.
It has some changes, several improvements and many bugfixes over the previous (not officially announced) 13.06. It is also the first official stable release of ejabberd Community after ejabberd 2.1.13. You are now pleased to use ejabberd community as reference for stable releases of ejabberd, from the master branch. ejabberd 2.1.x support is discontinued.
The most noticeable changes since 13.03-beta and 13.06 are:




We are pleased to announce the bugfix release ejabberd 2.1.13.
It includes a few bugfixes over 2.1.12:



Xiph.org has just posted the second in its series of videos on digital media concepts and techniques. It’s packed with information and demonstrations, and you’re sure to learn a huge amount. As an added bonus, it’s hosted by Monty, the creator of Ogg Vorbis (and many other amazing things). You couldn’t ask for a more qualified teacher.
Watch below, or on Xiph.org.
There is also a detailed write up.
by Jack Moffitt (jack@metajack.im) at February 26, 2013 00:00









ejabberd 2.1.10, 3.0.0-alpha-5 and exmpp 0.9.9 have been released, after several months of development. They contain a few bugfixes.
These are the major bugfixes:

ejabberd 2.1.9, ejabberd 3.0.0-alpha-4, and exmpp 0.9.8 have been released, after several months of development. They contain a lot of bugfixes, improvements and some new features.
This release includes a lot of bugfixes and improvements. This is just a short list of them:

ejabberd 2.1.6 has been released, after four months of development. It contains a lot of bugfixes, improvements and some new features.
This is a small list of changes:

ejabberd gets 8 years old. But no party yet, Yozhik is bugfixing 2.1.6 and testing 3.0.0-alpha-2.

The source and more photographs of hedgehogs pets.

After many months of planning, ejabberd and exmpp have been fully migrated to Git.
During the last 7 years, ejabberd source code was hosted at:
Starting now, ejabberd source code is natively in Git, and hosted at:
The minimal instructions to start using it are mentioned in:
http://www.process-one.net/en/ejabberd/downloads

Yes, ejabberd is already 7 years old.
Let's celebrate with a timeline of ejabberd, Erlang/OTP, XMPP/Jabber protocol, and Tkabber:
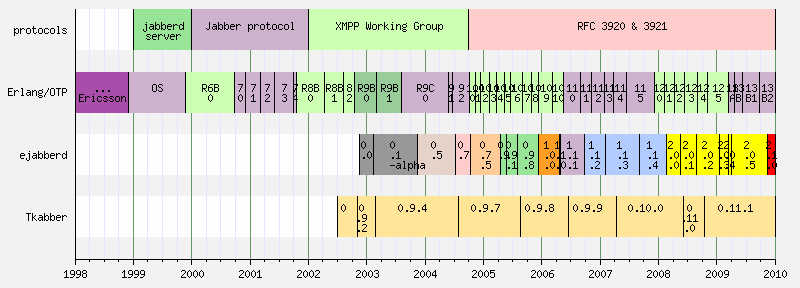
If you find any mistake, please comment. I built the graph using EasyTimeLine.pl, if you want the datafile, please comment.

To celebrate that ejabberd turns 6 years old, I've prepared a video that shows the history or ejabberd trunk SVN during those years: authors, acknowledgments, type of files, dates and releases. The video was built with code_swarm.
Download ejabberd-6-years-code.avi (12.5 MB) from: